
Penetration Testing
We offer Penetration Testing by OSCP (Offensive Security Certified Professional) credentialed team members. They are trained in the latest techniques and tools for threat detection, assessment and mitigation. Services are also available for Disaster Recovery and Remediation.
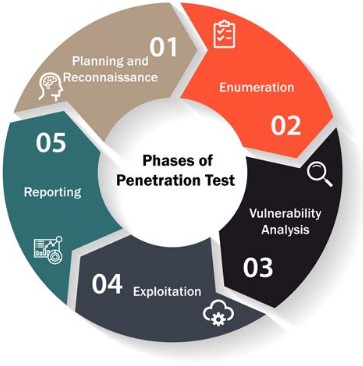
Lorem ipsum dolor sit amet, consectetur adipisicing elit, sed do eiusmod tempor incididunt ut labore et dolore magna aliqua. Ut enim ad minim veniam, quis nostrud exercitation ullamco laboris nisi ut aliquip ex ea commodo consequat. Duis aute irure dolor in reprehenderit in voluptate velit esse cillum dolore eu fugiat anim id
 Why do you need pentesting? This question is similar to “Why do you need to take medicine when you are ill?”
Why do you need pentesting? This question is similar to “Why do you need to take medicine when you are ill?”
The answer is quite simple. You need to conduct penetration testing because your applications might be vulnerable or insecure. Just like when the doctor checks you out and gives you a prescription when you are ill, pentesting helps you find those vulnerabilities in order for you to fix them and save your apps from getting hacked by Black Hat Hackers. Let’s face it! There is no application in the world that is 100% secure. This is a bitter truth but it’s the reality! Hence, it’s crucial that you pentest your apps.
Here Are The Top 5 Reasons Why You Need Penetration Testing:
1. To keep the company’s data protected
2. To fix the critical vulnerabilities
3. To protect PII data from Data Breaches
4. To become compliant, build a reputation in the market and trust amongst your stakeholders
5. To make your company sustainable
Keep the company's data protected There is a lot of information that needs to be kept confidential such as business plans, funding sources, employment details, customer data, and business strategies. Leaking these data can result in a potential loss to the company. Also, it can compromise the privacy of each and every person working at the company.
Fix the critical vulnerabilities
Some vulnerabilities are not so harmful as they don’t make much impact on the application. However, there are some serious and critical vulnerabilities, that if not fixed, can result in a great loss for the organization. For instance, vulnerabilities like Remote Code Execution (RCE) and Local File Inclusion/Remote File Inclusion can result in compromising the security of the server.
Protect PII data from Data Breaches
Many companies ask for users’ sensitive information such as credit card details, bank account details, passport, etc. This type of data is one of the main targets for most black hat hackers. Additionally, there are some vulnerabilities like SQL injection or weak data encryption that can result in massive data breaches, which can lead to a huge loss for a company. And, of course, don’t forget about the legal costs that this could cause, right? Authorities can normally take legal actions against companies that were not protecting their data.
Become compliant, build a reputation in the market and trust amongst your stakeholders Cyber Security is becoming one of the most important checkpoints for all organizations. It reflects the credibility of a company. If your business is taking security seriously, no customer will doubt twice to share their personal information with you. This is what trust does!
In addition to compliance requirements, penetration testing is a key aspect of any security program. The ever-changing threat landscape and the push of increasingly sophisticated attack methods indicate that organizations must constantly monitor and manage vulnerabilities.
Our customers usually conduct penetrationtests and external vulnerability scans to prepare and stay compliant with:
• PCI DSS (Payment Card Industry Data Security Standard) • ISO 27001:2013 • GDRP (General Data Protection Regulation) • TISAX (VDA ISA) • BSI-Grundschutz















